A new fileless ransomware has been discovered in the wild. This ransomware, titled SOREBRECT, injects malicious code into a valid system process (svchost.exe) on targeted systems and then self-destructs in order to evade detection by antivirus. This is unlike more generic "spray-and-pray" ransomware and has been designed to specifically target enterprise systems in various industries.
SOREBRECT also takes it a few steps further to cover its tracks and deletes the infected system’s event logs (using wevtutil.exe) that can provide forensic information such as files executed on the system, including the timestamps. These deletions deter analysis and prevent SOREBRECT’s activities from being traced.
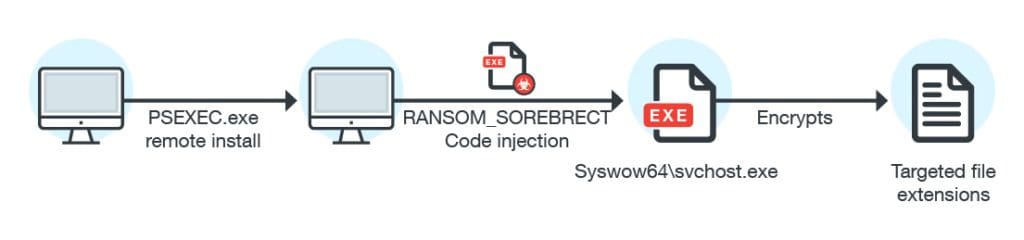
This ransomware uses Microsoft’s Sysinternals PsExec command-line utility to encrypt files after it has taken control of the machine. “PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs,” Trend Micro says.
SOREBRECT can also scramble the files of other computers connected to the infected machine through the local network. It scans the network for assets and open shares—folders, content or peripherals (i.e. printers) that others can readily access through the network. Once a live host is identified, it initiates a connection after discovering the shares. If the share has read-and-write access to it by the infected device, the share will also be encrypted.
SOREBRECT uses the Tor network protocol to anonymize its connection to its command-and-control (C&C) server.
According to Trend Micro, Sorebrect was initially targeting Middle Eastern countries like Kuwait and Lebanon, but since last month, this threat has started infecting machines in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
In February, Kaspersky researchers also discovered fileless malware that resided solely in the memory of the compromised computers, which was found targeting banks, telecommunication companies, and government organizations in 40 countries.
Kaspersky said: "Unfortunately the use of common tools combined with different tricks makes detection very hard. In fact, detection of this attack would be possible in RAM, network and registry only."
Below are the best practices suggested by TrendMicro:
Restrict user write permissions: By creating and enforcing IT policies, permissions are limited for users that do not require them, reducing risk of infection. Additionally, reviewing the permissions for each user in the Domain is a good starting point. Our managed services provide IT support and administration services, therefore Clients may open a ticket to request a review of folder permissions and shares as often as required.
Limit privilege for PsExec: PsExec is commonly used in enterprise networks, that provides system administrators flexibility with how they interact with remote machines - our managed services agents included. As a result, we are explicitly restricting PsExec execution policies. In addition, we have configured our scripts to set the PsExec to permissive levels on demand and setting the restrictions back upon completion.
Back up files: Cybercriminals use the potential loss of important and personal data as a fear tactic to coerce victims into paying the ransom. Therefore, backup is more important than ever. This is why our managed services support plans include a backup and disaster recovery solution.
Keep the system and network updated: Leaving network systems on auto-pilot is one of the worst decisions a company can make, especially when the company relies on its technology to do business. QWERTY Concepts managed services are designed for companies with and without internal IT personel, therefore we ensure redundant tasks are performed and notify those accountable when issues arise.
Foster a cybersecurity-aware workforce: User education and awareness helps improve everyone’s security posture. Like other malware, ransomware’s points of entry is typically through email and malicious downloads or domains. Organizations should conduct regular training to ensure that employees have a solid understanding of company security policy, procedures, and best practices.
Deploy multilayered security mechanisms: As ransomware matures in the threat landscape, we can only expect it to diversify in terms of attack methods and targets. There is no silver bullet for ransomware, which is why enterprises need a defense-in-depth approach to security where proactive security mechanisms are arrayed. At QWERTY Concepts, we continuously test and improve our security solutions. Additionally, our managed services includes an enterprise-level security appliance and content filtering as well many other endpoint security solutions.
