Over 120 managed service providers forgot to update a software plugin from 2017 and are now vulnerable to attacks.
Hackers used a two-year-old vulnerability in a remote management software to gain access to networks and deploy the GandCrab ransomware on customer workstations of managed service providers.
At least one company has been hit already, according to a report on Reddit, confirmed by cyber-security firm Huntress Labs.
The vulnerability used by the hackers is from the Kaseya plugin for the ConnectWise Manage software, a professional services automation (PSA) product used by many IT service providers.
The Kaseya VSA plugin integrates data from the Kaseya VSA, a remote monitoring and management solution with a ConnectWise dashboard.
Many small IT service providers and other types of managed service providers (MSPs) use the two applications to centralize data from their clients and manage customer workstations from a remote central location.
In November 2017, a security researcher named Alex Wilson, discovered an SQL injection vulnerability (CVE-2017-18362) in this plugin that could allow an attacker to create new administrator accounts on the main Kaseya app. He also published proof-of-concept code on GitHub that could automate the attack.
Kaseya released patches at the time, however it appears that many IT companies failed to install the updated Kaseya plugin on their ConnectWise dashboards, leaving their networks exposed.
Attacks exploiting this vulnerability started two weeks ago, towards the end of January 2019. One report posted on Reddit describes an incident at an MSP where hackers breached an MSP's network and then deployed GandCrab ransomware to 80 customer workstations.
A now-deleted tweet claimed that hackers used the same attack routine to infect other MSPs, locking more than 1,500 workstations.
ConnectWise has issued a security alert for their Manage product in response to the growing number of reports surrounding these ransomware attacks, advising users to update their ConnectWise Manage Kaseya plugin. The company said that only companies "who have the Plugin installed on their on-premises [Kaseya] VSA" are impacted.
In an interview with MSSP Alert, Kaseya executive VP of marketing and communications Taunia Kipp said they've identified 126 companies who failed to update the plugin and were still at risk.
"We posted a notification/support article to our support help desk and immediately started reaching out via phone/email to those identified who were at risk of impact with resolution," she said.
Huntress Lab researchers, who said they had "first-hand knowledge" of the incident involving 80 customer workstations that got infected with GandCrab.
Researchers from US firm Hold Security investigating Equifax after the recent Equifax security breach exposing details of 143 million customers have said its Argentine arm is also easily hackable.
It appears Equifax security measures are nothing but sloppy after revelations that its Argentinian database has 'admin' as both the username and password.
An employee portal, known as Veraz, provided access to personal details of 111 employees to researchers, by using the insecure logon credentials.
A further page contained 715 complaints from customers, each with social security numbers being stored in plain text.
All that was protecting the sensitive personal information was what Hold security advisor Brian Krebs called “perhaps the most easy-to-guess password combination ever.”
“To me, this is just negligence,” founder Alex Holden added.
“In this case, their approach to security was just abysmal, and it’s hard to believe the rest of their operations are much better.”
Krebs meanwhile described the firm as “sloppy” as representatives took the offending portal offline.
Cointelegraph reported the giant data theft had occurred several months ago but only came to light six weeks afterwards as officials sought to keep the situation under control. A separate inquiry is currently ongoing regarding three investors who sold $18 mln worth of shares between the date of the hack discovery and the public disclosure.
In the recent days Equifax has been heavily criticized by the public, citing that Equifax should be shut down and pointing out the irony to report irresponsible consumers.
I don't believe in capital punishment for humans, but I do believe in it for corporations. @Equifax should be put to death. #equifaxbreach
— Scott Santens (@scottsantens) September 8, 2017
So I'm not the only one that gets a free copy of my credit report. Got it.#Equifax#EquifaxBreach
— Ise Malaka (@ise_malaka) September 7, 2017
I've never done business with #Equifax, yet they had and compromised my sensitive data. That is beyond unacceptable—they should be shut down
— Eli Beckman (@elihbeckman) September 11, 2017
This is not the first security breach that we have learned of this year. Earlier this year, it was reported that Equifax had yet another security breach in April of 2016. It is reported that from April 18, 2016 to March 29, 2017 a copy of the 2016 W-2 form may have been downloaded during the breach, providing personal information including name, address, email, phone, social security number, employer identification number, and wage tax information.
In conclusion, security should be a top concern in the modern era. Stanley Kaytovich, an IT director at QWERTY Concepts, stated "There is a very important lesson here for consumers and corporations alike. Using a secure password should not be negotiable." QWERTY Concepts provides IT support services in NJ.
Phishing emails convinced staff at MacEwan University that a client was changing its bank account details. The staff then paid money into the fraudulent account.
Since the online phishing scam, the university, located in Alberta, Canada, is auditing its business practices. Police were able to trace most of the funds to accounts in Hong Kong and Montreal, however no charges have been files at this time. The scam came to light when the real client complained of non-payment.
"There is never a good time for something like this to happen," university spokesperson David Beharry said in a statement.
"As our students come back to start the new academic year, we want to assure them and the community that our IT systems were not compromised during this incident."
Phishing is a type of fraud performed over the internet where the scammers send emails that mimic reputable business entities (and individuals). The purpose of these phishing attacks is to entice people to give up personal information.
Mr Beharry also said the university was working to ensure that this fraud would not impact future educational or business operations.
A preliminary audit found that protocols around changing banking information were "inadequate" and staff missed a number of opportunities to identify the fraud.
Where you are a business, doctors office, or a university - certain security protocols are essential. This is why QWERTY Concepts includes essential security service as part of their managed IT services in NJ.
In these recent attacks cyber criminals target victims using social media networks, specifically those individuals inside financial organizations and those who make financial transactions. These victims were then called using the phone by the attacker posing as bank employees, who then used social engineering tactics to trick the victim to install an "update" to the bank’s security module.
The victims, worried that they would lose access to their account, complied by installing a Chrome extension called Interface Online offered by Internet Security Online. The extension was available on Tuesday in the Chrome store. As it was discovered, Google took it down. This scam was first discovered in Brazil, but expect this soon in the US and Europe.
The pressure-filled phone call to the banks includes instructions on how to update the supposed security module. The victim is provided with a web address over the phone and when they click “Install,” they are redirected to the extension’s installation page, hosted in the Chrome Store. The cyber criminal keeps the victim on the line throughout the installation process and once it’s complete, has them test their access to the corporate bank account. As they enter their credentials, the data is sent to the attackers in the background.
“I’ve had the opportunity to listen to one of those calls and I must admit that they make it in a professional way,” Marinho told Threatpost.
“In my opinion, the criminals are shifting from the traditional [malicious spam] to targeted and more creative attack methods here in Brazil,” Marinho said. ‘It’s getting common to have victims reporting that they are receiving phone calls from someone pretending to be from a bank and urging the victim to do something, like installing a fake security module, this case, or asking them to type the token combination on a fake website.”
These attacks are the latest in a growing trend of fraud exploiting Chrome extensions. In the recent weeks, researchers have reported at least eight popular Chrome plugins had been hijacked and were being abused to manipulate internet traffic and serve ads in the browser.
Warn your accounting team that this is a new scam they need to watch out for. Also, ensure your company systems are managed by a professional IT service provider to monitor and maintain the network and IT systems. It is important that the provider implements comprehensive security services as part of their offering.
Reference: https://isc.sans.edu/forums/diary/BankerGoogleChromeExtensiontargetingBrazil/22722/
As in previous example of ransomware attacks, cybercriminals usually go straight for the end users. There are times however, they take a less direct approach, as they did with an adware campaign that targeted Google Chrome users.
Copyfish is a translation plug-in for Google Chrome. By no means is it one of the most used Chrome extensions, but based on the most recent information from the Google's Web Store, it had somewhere over 30,000 users. To a criminal, that is a fairly large pool of potential victims.
You may not have heard of online ad fraud and clickjacking, but they're very widespread problems. It's difficult to know exactly how widespread, too, because they often go unreported.
On Friday, an unknown hacker hijacked the Copyfish Chrome extension from its original authors and pushed an update that inserted ads in people's web pages.
The hack took place because one of the Copyfish developers fell for a simple phishing trick and accessed a link in an email he thought he received from the Chrome team. In reality, the email came from the phisher and urged the Copyfish developer to update his extension, or it would be removed from the Chrome Web Store.
When the developer accessed the link, he was redirected to a copy of the Google account login page, where the developer then entered his credentials for the developer account.
The login page was hosted on chromedev.freshdesk.com, and surprisingly the extension's developer didn't think it was strange, even if Google has hosted its support desks on its own domains for more than a decade.
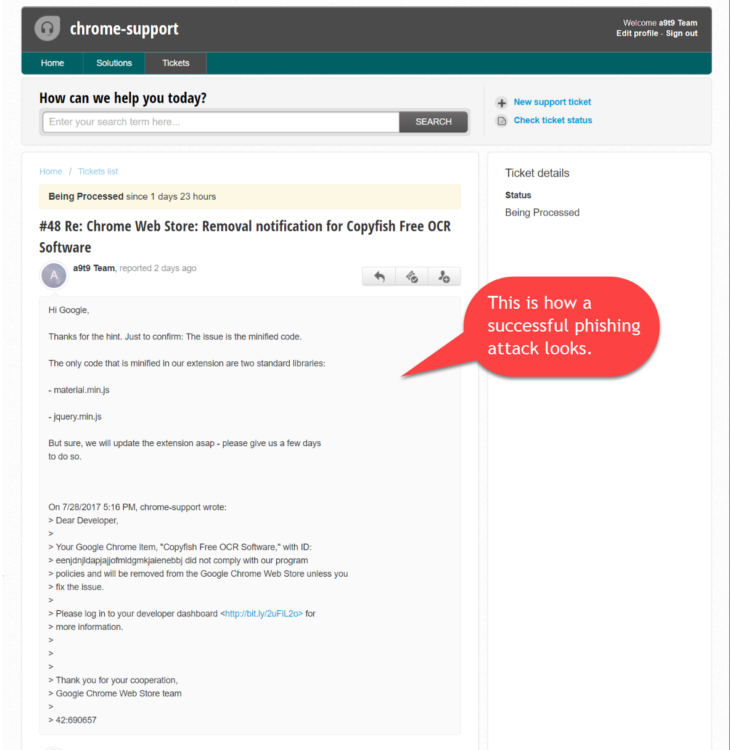
A day later, the hacker had pushed a malicious update (v2.8.5) for the Chrome Copyfish extension, which is a pretty powerful tool for extracting text from images and PDF files.
The update added extra JavaScript code that loaded ads on all the pages a user viewed. Despite this intrusive behavior, it took Copyfish developers a full day to realize what had happened.
Unfortunately, by that point, the hacker had transferred the extension to his own developer account, out of the reach of the original authors, who were desperately trying to reach a Google staffer to have the extension pulled down.
At the time of writing, the extension is still under the hijacker's control. Users are advised to remove it from their browsers. The Copyfish team says its Firefox add-on is safe and under their control.
QWERTY Concepts, an IT support provider based in New Jersey, always emphasizes on the risks that end users pose to company networks. Stanley Kaytovich, an IT director stated "Protection starts at the endpoint". "End users pose one of the biggest risks to a company security noawdays" he stated. QWERTY Concepts is a provider of IT services for businesses. "Security is always a top consideration for any implementation" he stated.
According to a report released by the Identity Theft Resource Center and CyberScout, data breaches are running 29% above last year. Hacking was the leading cause of data breaches nationwide, more than 790 so far this year.
Although two-thirds of data breach notifications or public notices did not report the number of records compromised, more than 12 million records have been exposed.
“Only 33 percent of data breaches reported this year have made the number of records exposed publicly available,” said Karen A. Barney, director of research and publications at Identity Theft Resource Center, an increase of 13 percent over 2016 mid-year numbers.
The resource center tracks breaches in the categories of financial, health care and medical, government and military, education and business.
More than half of all beaches this year have occurred in business, followed by health care and medical. Breaches in the medical and health-care industry are most likely to include the number of records involved. More than 80 percent of breaches in 2017 that were reported to Health & Human Services included the number of records.
According to the resource center, a data breach occurs when a name is released in connection with a Social Security number, driver’s license number, medical or financial record. The exposure is tracked when it occurs because of a phishing or hacking attack, theft, negligence or error.
“Exposure of the Social Security number is the primary trigger across the board for a state data breach notification,” Barney said.
Exposure that includes a user name or email address in combination with a password or security information that would allow access to an online account may also trigger a notification in California, the first state to enact a data security breach notification law.
This year, personal information has been compromised by the unauthorized acquisition of data at universities, businesses, banks, medical and government institutions:
Major breaches involving the exposure of names and other information have also occurred this year:
Since 2005, there have been almost 7,700 data breaches which have exposed more than 900 million records in the U.S. according to the resource center.
With the rise in dependability on technology and on the internet, cybercrime is also on the rise. To meet the demand, there is a rising trend of social engineering sites on the dark web, which make malicious hacking a point-and-click exercise. You read correctly, you can now pay for a service to help you commit crime and a new report describes two more sites that were discovered by security researchers.
The first is Ovidiy Stealer, found by Proofpoint, which steals passwords and is marketed on Russian-language website for 7 bucks. It's regularly updated and the sales seem to skyrocket.
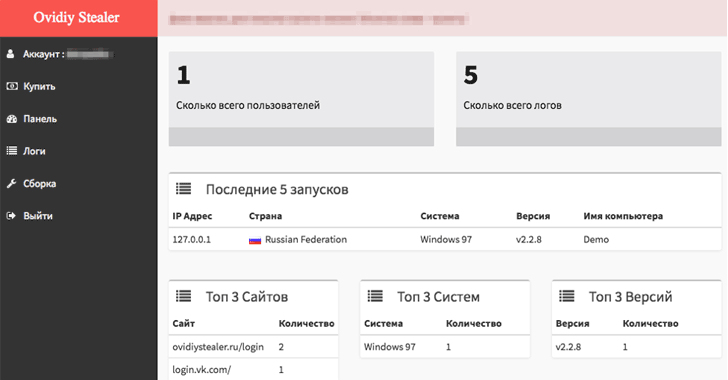
The Ovidiy Stealer malware currently has several versions in the wild, targeting people around the world. It is believed that the malware is currently being spread via email as executable attachments, compressed executable attachments, and links to an executable download. It is also likely spread via file hosting / cracking / keygen sites, where it poses as other software or tools.
Since it has been discovered, the content of this site has been removed. The site itself however, appears to still be online. Below is a list of some of the observed filenames that disguise the malware:
Ovidiy Stealer is written in .NET and most samples are packed with with either .NET Reactor or Confuser. Upon execution the malware will remain in the directory in which it was installed, and where it will carry out tasks. Somewhat surprisingly, there is no persistence mechanism built into this malware, so on reboot it will cease to run, but the file will remain on the victim machine.
Ovidiy Stealer is modular and contains functionality to target a multiple applications -- primarily browsers -- listed below.
The second is Hacksh*t, discovered by the Netskope Threat Research Labs, and is a Phishing-as-a-Service (PhaaS) platform that offers low cost, "automated solution for the beginner scammers."
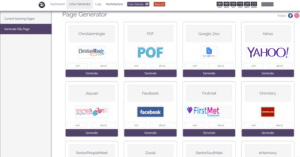
This platform offers free trial accounts to test their hacking tutorials and tricks to make easy money. "The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks," Netskope researcher Ashwin Vamshi says.
The Hacksh*t website had a video demonstration appealing users to learning hacking, meeting hackers online and making money. It allows wannabe hackers (subscribers) to generate their unique phishing pages for several services, including Yahoo, Facebook, and Google's Gmail. "The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link."
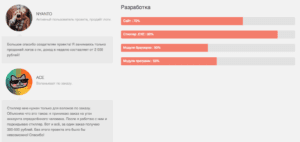
According to Proofpoint, "Like many other markets with many choices, the malware market is competitive and developers must market the strengths and benefits of their products in order to attract buyers. To help drive sales, the development team includes statistics on the progress of certain modules, and other plans for future releases of the malware. In addition, the site includes “testimonials" from satisfied customers, presumably to demonstrate to other would-be criminals that they can be profitable when using Ovidiy Stealer."
Below is a screen capture of the reviews and development progress of Odiviy Stealer. The user ACE’s comments translate to English as: “I only need the stealer for burglary on order. I explain what it is: I accept an order for the hijacking of a certain person's account. After I work with him and install the stealer. That's all, for one order I get 300-500 rubles. Without this project it would be impossible! Thank you!”
It is inevitable that more and more software engineering services will surface. With the internet connecting people worldwide, it certainly comes with its challenges. This is a huge risk for businesses, because they are usually the targets of malware and phishing attacks.
This is why it is important to implement corporate policies and security services to protect company data. Backup and disaster recovery is also a huge component and a requirement in many instances to become operational after an infection.
Of course proactive measures are the first line of defense. Therefore, it is critical for companies to hire knowledgeable IT providers and staff to ensure their data is protected. QWERTY Concepts includes essential security services, such as anti-virus, anti-malware, inbound and outbound email security, backup & disaster recovery, and network security with web content filtering as part of its monthly managed services offering. Schedule a free technology assessment today!
After two recent ransomware cyber attacks disrupted businesses, factories, hospitals and schools in over 150 countries, there are many lessons to be learned. The WannaCry ransomware was developed to take control of system data. It encrypted files as soon as the virus became active and demanded a ransom to be paid via Bitcoin, a cryptocurrency which makes funds transfer anonymous. For those companies without proper backup solutions or business continuity planning, this was extremely costly and possibly detrimental to not only the companies, but the consumers being provided the products and or services by these businesses.
According to Andrew Douthwaite, of business.com, these types of cyber attacks will only grow in popularity, it's unavoidable. Here are a number of key steps that business must take to protect themselves from having to deal with a prompt window demanding a ransomware payment, which rarely leads to successful recovery.
Executives need to recognize that rogue events, such as ransomware infections, denial of service interruptions, and direct cyber attacks, affect a company's bottom line. Technology allows businesses to operate at a fantastic speed, but many underestimate the amount of risk this carries. For companies that provide mission-critical services, this risk is tenfold. For them, downtime means hemorrhaging revenue and a sudden erosion of consumer trust. When ransomware is discussed at the highest level, only then can the right strategies be implemented successfully.
The executives and managers should also consider , hiring a professional IT Support company that can assist with the review, planning, and implementation of strategies based on business needs. These companies have real-world experience and knowledge that can be very beneficial to designing the right solution.
Even the best cyber security systems are vulnerable to an uneducated workforce. Businesses suffer when users perform simple mistakes like downloading infected email attachments, browsing infected sites, and using common and easy-to-guess passwords.
Cybersecurity practices don't need to be complicated. Many managed service providers will provide a list of best practices that can be translated or directly taught to employees, safeguarding your company’s data and time. Also, email security platforms should thwart any malicious emails from reaching end users in the first place. Most decent managed service providers include many essential security services as part of their standard managed IT service plans.
Many systems and processes will "feel" secure, even to educated analysts. Having a third-party perform an investigative review will highlight any blind spots. Existing legacy systems should be upgraded where possible. In the wake of WannaCry, this was one of the reasons that the U.K.’s National Health Service had to turn away non-emergency patients.
When legacy systems are a necessity, they should be protected with unprecedented security – robust firewalls, URL and IP filtering and strict user regulations. Outsourcing cyber security protection is a popular choice for good reason. In-house teams deserve an extra pair of eyes and professional tool sets.
Software updates have long been the bane of IT departments for good reason – updates break things. However, users who were running the latest versions of Microsoft Windows were almost invulnerable to the WannaCry virus. Having an upgrade and maintenance cycle that makes sense is vital, and unsupported operating systems should be avoided at all costs.
Instead of putting upgrades off, having a plan for implementing future patches will safeguard against most attacks. When large companies fall victim to cyber attacks due to outdated software, and this fact is publicized, public confidence waivers.
Not only do backups need to be performed regularly, they need to be secure and available. It’s important in the wake of an attack that businesses understand which data has been lost and which is recoverable. Having your security evaluated will point out which systems deserve most frequent backups and where optimizations can be made. With many off-the-shelf backup solutions or MSP versions of BDRs, the backups reside on a Windows computer and are connected via a network share. In the event of a ransomware, these shares also get encrypted, prohibiting access to perform a restoration. This is a serious problem and having a backup that is encrypted is like not having a backup at all.
For instance, the QWERTY Concepts latest backup and disaster recovery (BDR) solution is encrypted on a Linux file system that does not rely on a Windows share to perform backups, therefore protected from being encrypted. Selecting the right backup solution can be the difference between the "life and death" of a business.
Furthermore, continuity planning is just as important as backing up data. All systems can fail, even mission critical ones. What’s key is having a plan for getting things running again. Documentation is key. You don’t want to be scrambling for ideas when employees are stressed and in a rush to get everything back online. Following a system outage, an up-to-date playbook will lead you out of the dark.
WannaCry and Petya signaled to hackers and state-sponsored groups that the business world remains highly vulnerable to cyber attacks. Luckily, there are many solutions companies can turn to. Security specialists worldwide are working together more than ever before. It’s easy to forget that you're not alone in protecting yourself against cyber risks.
User computers and servers should be protected by multiple layers of security, ensuring that attackers and malicious software cannot move laterally. There will always be weak points. Being prepared, however, means never giving up looking for them.
A massive attack, triggered by a version of the GoldenEye or Petya ransomware is currently claiming victims around the world. Unlike other families of ransomware, #GoldenEye does not encrypt individual files, but rather the entire hard disk drive. It then reboots it to prevent the user from accessing that information. When the encryption process is complete, #GoldenEye forcefully crashes the computer and asks for $300 as ransom.
What is unique about #GoldenEye is that unlike other ransomware, this variant has two layers of encryption: once that encrypts files on the computer and another one that encrypts NTFS filesystems. This approach prevents victim computers from being booted up into Windows.
Additionally, after the encryption process is complete, the ransomware has a specialized routine that forcefully crashes the computer to trigger a reboot that renders the computer unusable until the $300 ransom is paid.
According to BitDefender Labs, some infections with GoldenEye/Petya have been triggered by a compromised update of the MeDOC accounting software. It was first intercepted by their customers in Ukraine, therefore confirming the MeDOC update as the infection vector. This makes Ukraine "patient zero" from where the infection spread across networks to headquarters and/or satellite offices.
"Our initial investigation reveals that it spreads automatically from one computer to another using multiple vulnerabilities in the operating system, including the EternalBlue exploit that grabbed the headlines during the #WannaCry attack.", stated BitDefender.
BitDefender Labs also noted that "Several critical infrastructure institutions in Ukraine have already been taken offline." and "We strongly advise all companies who have offices in Ukraine to be on the lookout and to monitor VPN connections to other branches."
It is probably obvious, but everyone is at risk. Even if you are on the latest operating system with the latest Antivirus detection, it is important for all end users to be aware and avoid clicking on files in suspicious emails. It has been confirmed that several companies so far have fallen victim to the #GoldenEye/#Petya ransomware.
Chernobyl’s radiation monitoring system, DLA Piper law firm, pharma company Merck, a number of banks, an airport, the Kiev metro, Danish shipping and energy company Maersk, British advertiser WPP and Russian oil industry company Rosnoft. The attacks were widespread in Ukraine, affecting Ukrenergo, the state power distributor, and several of the country’s banks.
The email address used to get payment confirmation for the ransom has been suspected by Posteo. This means that all payments will be unable to get validated, and therefore will not receive the decryption key. As a result, do not pay the ransom. You'll lose your data anyway, but will also contribute to fund these cyber terrorists for further development of malware.
Our managed services suite includes BitDefender for its endpoint security, who released a statement confirming that Bitdefender blocks the currently known samples of the new #GoldenEye variant and "If you are running a Bitdefender security solution for consumer or business, your computers are not in danger".
Additionally, our managed service plans include email security to block spam and malware externally, before even making it to the network, reducing the risk of infections.
A new fileless ransomware has been discovered in the wild. This ransomware, titled SOREBRECT, injects malicious code into a valid system process (svchost.exe) on targeted systems and then self-destructs in order to evade detection by antivirus. This is unlike more generic "spray-and-pray" ransomware and has been designed to specifically target enterprise systems in various industries.
SOREBRECT also takes it a few steps further to cover its tracks and deletes the infected system’s event logs (using wevtutil.exe) that can provide forensic information such as files executed on the system, including the timestamps. These deletions deter analysis and prevent SOREBRECT’s activities from being traced.
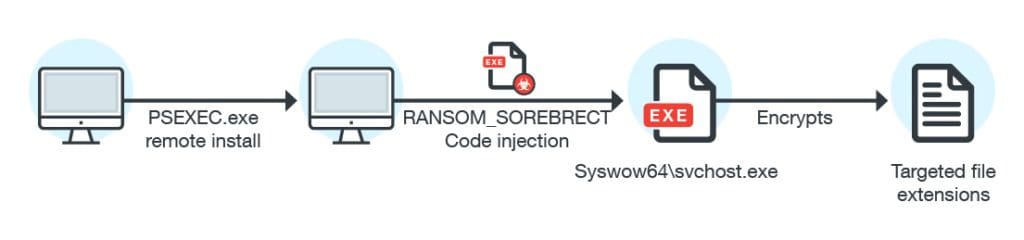
This ransomware uses Microsoft’s Sysinternals PsExec command-line utility to encrypt files after it has taken control of the machine. “PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs,” Trend Micro says.
SOREBRECT can also scramble the files of other computers connected to the infected machine through the local network. It scans the network for assets and open shares—folders, content or peripherals (i.e. printers) that others can readily access through the network. Once a live host is identified, it initiates a connection after discovering the shares. If the share has read-and-write access to it by the infected device, the share will also be encrypted.
SOREBRECT uses the Tor network protocol to anonymize its connection to its command-and-control (C&C) server.
According to Trend Micro, Sorebrect was initially targeting Middle Eastern countries like Kuwait and Lebanon, but since last month, this threat has started infecting machines in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
In February, Kaspersky researchers also discovered fileless malware that resided solely in the memory of the compromised computers, which was found targeting banks, telecommunication companies, and government organizations in 40 countries.
Kaspersky said: "Unfortunately the use of common tools combined with different tricks makes detection very hard. In fact, detection of this attack would be possible in RAM, network and registry only."
Below are the best practices suggested by TrendMicro:
Restrict user write permissions: By creating and enforcing IT policies, permissions are limited for users that do not require them, reducing risk of infection. Additionally, reviewing the permissions for each user in the Domain is a good starting point. Our managed services provide IT support and administration services, therefore Clients may open a ticket to request a review of folder permissions and shares as often as required.
Limit privilege for PsExec: PsExec is commonly used in enterprise networks, that provides system administrators flexibility with how they interact with remote machines - our managed services agents included. As a result, we are explicitly restricting PsExec execution policies. In addition, we have configured our scripts to set the PsExec to permissive levels on demand and setting the restrictions back upon completion.
Back up files: Cybercriminals use the potential loss of important and personal data as a fear tactic to coerce victims into paying the ransom. Therefore, backup is more important than ever. This is why our managed services support plans include a backup and disaster recovery solution.
Keep the system and network updated: Leaving network systems on auto-pilot is one of the worst decisions a company can make, especially when the company relies on its technology to do business. QWERTY Concepts managed services are designed for companies with and without internal IT personel, therefore we ensure redundant tasks are performed and notify those accountable when issues arise.
Foster a cybersecurity-aware workforce: User education and awareness helps improve everyone’s security posture. Like other malware, ransomware’s points of entry is typically through email and malicious downloads or domains. Organizations should conduct regular training to ensure that employees have a solid understanding of company security policy, procedures, and best practices.
Deploy multilayered security mechanisms: As ransomware matures in the threat landscape, we can only expect it to diversify in terms of attack methods and targets. There is no silver bullet for ransomware, which is why enterprises need a defense-in-depth approach to security where proactive security mechanisms are arrayed. At QWERTY Concepts, we continuously test and improve our security solutions. Additionally, our managed services includes an enterprise-level security appliance and content filtering as well many other endpoint security solutions.
