In yet another phishing email hoax, the New York State DMV is now cautioning consumers against an email "phishing" campaign. This phishing attempt sends a notice to email users stating they must pay a ticket within 48 hours or their license will be revoked. While the notice is made to appear as if it comes from DMV, it is a hoax.
Though the recent press release is from the New York State Department of Motor Vehicles, campaigns for other states may be soon be phishing for personal information as well. The NY DMV advises that the "Email falsely claims to be from New York State DMV". The DMV also advises to "not click on links".
The phishing email hoax targets New York drivers, stating they have 48 hours to pay a fine or have their driver's license revoked. The NY DMV alerted motorists that the scam is just bait to entice them to click on a “payment” link. Once clicked, it will in turn infect their workstation with malware. The DMV does not know how many people have been affected, but Owen McShane, director of investigations at New York State DMV, said calls came in from New York City, Albany and Syracuse.
Olenick also went into more detail stating "The malware being dropped came in two categories. The first simply placed a tracking tool on the victim's computer to see what websites were visited; and the second, more nefarious, attempted to acquire a variety of personally identifiable information, such as names, Social Security numbers, date of birth and credit card information."
There are several red flags that show the email is a scam. The supplied links lead to sites without an ny.gov URL, tied to the fact that the state would never make such a request. The hoax email lists a reference number and then reads something like this:
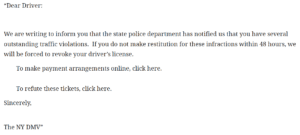
“The Department of Motor Vehicles does not send emails urging motorists to pay traffic tickets within 48 hours or lose your license,” said Terri Egan, DMV deputy executive commissioner, in a statement.
We suggest you send your employees, co-workers, friends, and family an email about this scam, feel free to copy/paste/edit:
"Here is a reminder that you need to be alert for fake emails that look like they come from your local police or State Dept of Motor Vehicles (DMV) claiming you have a traffic violation. At the moment, there is a local scam in New York that falsely states you have outstanding violations you need to either pay for or refute, and if you don't your license will be revoked. This scam may spread to the rest of America soon. Remember that citations are never emailed with links in them, or sent out with an email attachment, and report scams like this to your local police department."
Obviously, an end-user who was trained to spot these red flags like this would have thought before they clicked. Additionally, email security solutions will likely trap these types of emails before they reach the mailbox.
We strongly suggest you get a quote for email security services for your organization - you'd be surprised how affordable they are. Contact us for a quote, today!
Reference: https://dmv.ny.gov/press-release/press-release-06-01-2017
DocuSign, a major provider of electronic signature technology based in San Francisco, admitted that a series of recent phishing malware attacks targeting its customers and users was the result of a data breach at one of its computer systems. The company stresses that the data stolen was limited to customer and user email addresses. The incident is especially dangerous, because it allows attackers to target users who may already be expecting emails from DocuSign. This form of attack is known as phishing attempts.
DocuSign warned on May 9 that it was tracking a malicious email campaign where the subject line reads, “Completed: docusign.com – Wire Transfer Instructions for recipient-name Document Ready for Signature.” The email contained a link to a downloadable Microsoft Word document. The attachment contains malware, and tricks users into activating Word's macro feature, which will download and install malware on the user's workstation.
The company initially dismissed that the messages were associated with DocuSign and that they were sent from a malicious third party. However, in an update on Monday, DocuSign confirmed that this malicious third party was able to send the messages to DocuSign's customers and users because it had broken in and stolen their list of customers and users.
“As part of our ongoing investigation, today we confirmed that a malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email,” DocuSign wrote in an alert posted to its site. “A complete forensic analysis has confirmed that only email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.”
They are advising customers to filter or delete any emails with specific subject lines. These email subjects look something like:
Completed: [domain name] – "Wire transfer for recipient-name Document Ready for Signature"
Completed [domain name/email address] – "Accounting Invoice [Number] Document Ready for Signature"
Subject: “Legal acknowledgement for [recipient username] Document is Ready for Signature”
Since the recent newsworthy security breaches, it is becoming critical to educate employees on identifying and handling potential threats. Bringing awareness is not enough, however. Due to the human factor, many email solutions, whether they are cloud-based or on-premise, integrate with outside email security services. These that filter and quarantine potential threats before they arrive to the email server and even network. QWERTY Concepts, provides email security services for their cloud platform, office 365, and to on-premise email servers. Click here to receive a free consultation and quote.
The company is asking people to forward suspicious emails related to DocuSign to [email protected].
