With the rise in dependability on technology and on the internet, cybercrime is also on the rise. To meet the demand, there is a rising trend of social engineering sites on the dark web, which make malicious hacking a point-and-click exercise. You read correctly, you can now pay for a service to help you commit crime and a new report describes two more sites that were discovered by security researchers.
The first is Ovidiy Stealer, found by Proofpoint, which steals passwords and is marketed on Russian-language website for 7 bucks. It's regularly updated and the sales seem to skyrocket.
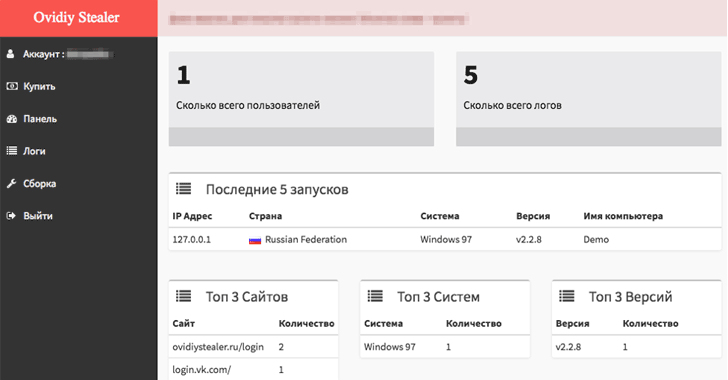
The Ovidiy Stealer malware currently has several versions in the wild, targeting people around the world. It is believed that the malware is currently being spread via email as executable attachments, compressed executable attachments, and links to an executable download. It is also likely spread via file hosting / cracking / keygen sites, where it poses as other software or tools.
Since it has been discovered, the content of this site has been removed. The site itself however, appears to still be online. Below is a list of some of the observed filenames that disguise the malware:
Ovidiy Stealer is written in .NET and most samples are packed with with either .NET Reactor or Confuser. Upon execution the malware will remain in the directory in which it was installed, and where it will carry out tasks. Somewhat surprisingly, there is no persistence mechanism built into this malware, so on reboot it will cease to run, but the file will remain on the victim machine.
Ovidiy Stealer is modular and contains functionality to target a multiple applications -- primarily browsers -- listed below.
The second is Hacksh*t, discovered by the Netskope Threat Research Labs, and is a Phishing-as-a-Service (PhaaS) platform that offers low cost, "automated solution for the beginner scammers."
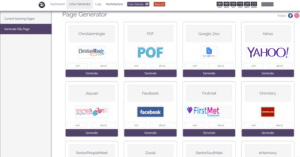
This platform offers free trial accounts to test their hacking tutorials and tricks to make easy money. "The marketplace is a portal that offers services to purchase and sell for carrying out the phishing attacks," Netskope researcher Ashwin Vamshi says.
The Hacksh*t website had a video demonstration appealing users to learning hacking, meeting hackers online and making money. It allows wannabe hackers (subscribers) to generate their unique phishing pages for several services, including Yahoo, Facebook, and Google's Gmail. "The attacker then generates a phished page from the page/generator link and logs into the email account of the compromised victim, views all the contacts and sends an email embedded with the phished link."
According to Proofpoint, "Like many other markets with many choices, the malware market is competitive and developers must market the strengths and benefits of their products in order to attract buyers. To help drive sales, the development team includes statistics on the progress of certain modules, and other plans for future releases of the malware. In addition, the site includes “testimonials" from satisfied customers, presumably to demonstrate to other would-be criminals that they can be profitable when using Ovidiy Stealer."
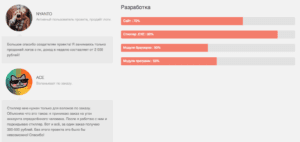
Below is a screen capture of the reviews and development progress of Odiviy Stealer. The user ACE’s comments translate to English as: “I only need the stealer for burglary on order. I explain what it is: I accept an order for the hijacking of a certain person's account. After I work with him and install the stealer. That's all, for one order I get 300-500 rubles. Without this project it would be impossible! Thank you!”
It is inevitable that more and more software engineering services will surface. With the internet connecting people worldwide, it certainly comes with its challenges. This is a huge risk for businesses, because they are usually the targets of malware and phishing attacks.
This is why it is important to implement corporate policies and security services to protect company data. Backup and disaster recovery is also a huge component and a requirement in many instances to become operational after an infection.
Of course proactive measures are the first line of defense. Therefore, it is critical for companies to hire knowledgeable IT providers and staff to ensure their data is protected. QWERTY Concepts includes essential security services, such as anti-virus, anti-malware, inbound and outbound email security, backup & disaster recovery, and network security with web content filtering as part of its monthly managed services offering. Schedule a free technology assessment today!
In yet another phishing email hoax, the New York State DMV is now cautioning consumers against an email "phishing" campaign. This phishing attempt sends a notice to email users stating they must pay a ticket within 48 hours or their license will be revoked. While the notice is made to appear as if it comes from DMV, it is a hoax.
Though the recent press release is from the New York State Department of Motor Vehicles, campaigns for other states may be soon be phishing for personal information as well. The NY DMV advises that the "Email falsely claims to be from New York State DMV". The DMV also advises to "not click on links".
The phishing email hoax targets New York drivers, stating they have 48 hours to pay a fine or have their driver's license revoked. The NY DMV alerted motorists that the scam is just bait to entice them to click on a “payment” link. Once clicked, it will in turn infect their workstation with malware. The DMV does not know how many people have been affected, but Owen McShane, director of investigations at New York State DMV, said calls came in from New York City, Albany and Syracuse.
Olenick also went into more detail stating "The malware being dropped came in two categories. The first simply placed a tracking tool on the victim's computer to see what websites were visited; and the second, more nefarious, attempted to acquire a variety of personally identifiable information, such as names, Social Security numbers, date of birth and credit card information."
There are several red flags that show the email is a scam. The supplied links lead to sites without an ny.gov URL, tied to the fact that the state would never make such a request. The hoax email lists a reference number and then reads something like this:
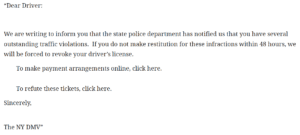
“The Department of Motor Vehicles does not send emails urging motorists to pay traffic tickets within 48 hours or lose your license,” said Terri Egan, DMV deputy executive commissioner, in a statement.
We suggest you send your employees, co-workers, friends, and family an email about this scam, feel free to copy/paste/edit:
"Here is a reminder that you need to be alert for fake emails that look like they come from your local police or State Dept of Motor Vehicles (DMV) claiming you have a traffic violation. At the moment, there is a local scam in New York that falsely states you have outstanding violations you need to either pay for or refute, and if you don't your license will be revoked. This scam may spread to the rest of America soon. Remember that citations are never emailed with links in them, or sent out with an email attachment, and report scams like this to your local police department."
Obviously, an end-user who was trained to spot these red flags like this would have thought before they clicked. Additionally, email security solutions will likely trap these types of emails before they reach the mailbox.
We strongly suggest you get a quote for email security services for your organization - you'd be surprised how affordable they are. Contact us for a quote, today!
Reference: https://dmv.ny.gov/press-release/press-release-06-01-2017
DocuSign, a major provider of electronic signature technology based in San Francisco, admitted that a series of recent phishing malware attacks targeting its customers and users was the result of a data breach at one of its computer systems. The company stresses that the data stolen was limited to customer and user email addresses. The incident is especially dangerous, because it allows attackers to target users who may already be expecting emails from DocuSign. This form of attack is known as phishing attempts.
DocuSign warned on May 9 that it was tracking a malicious email campaign where the subject line reads, “Completed: docusign.com – Wire Transfer Instructions for recipient-name Document Ready for Signature.” The email contained a link to a downloadable Microsoft Word document. The attachment contains malware, and tricks users into activating Word's macro feature, which will download and install malware on the user's workstation.
The company initially dismissed that the messages were associated with DocuSign and that they were sent from a malicious third party. However, in an update on Monday, DocuSign confirmed that this malicious third party was able to send the messages to DocuSign's customers and users because it had broken in and stolen their list of customers and users.
“As part of our ongoing investigation, today we confirmed that a malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email,” DocuSign wrote in an alert posted to its site. “A complete forensic analysis has confirmed that only email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure.”
They are advising customers to filter or delete any emails with specific subject lines. These email subjects look something like:
Completed: [domain name] – "Wire transfer for recipient-name Document Ready for Signature"
Completed [domain name/email address] – "Accounting Invoice [Number] Document Ready for Signature"
Subject: “Legal acknowledgement for [recipient username] Document is Ready for Signature”
Since the recent newsworthy security breaches, it is becoming critical to educate employees on identifying and handling potential threats. Bringing awareness is not enough, however. Due to the human factor, many email solutions, whether they are cloud-based or on-premise, integrate with outside email security services. These that filter and quarantine potential threats before they arrive to the email server and even network. QWERTY Concepts, provides email security services for their cloud platform, office 365, and to on-premise email servers. Click here to receive a free consultation and quote.
The company is asking people to forward suspicious emails related to DocuSign to [email protected].
 A botnet that infects and exploits poorly-maintained Linux servers has been used to launch a spate of large DDoS attacks targeting DNS and other infrastructure, Akamai’s Prolexic division has warned.
A botnet that infects and exploits poorly-maintained Linux servers has been used to launch a spate of large DDoS attacks targeting DNS and other infrastructure, Akamai’s Prolexic division has warned.
Dubbed the ‘IptabLes and IptabLex botnet’ the attack target versions of Apache Struts and Tomcat, as well as some running Elasticsearch that have not been patched against a clutch of vulnerabilities.
Once compromised, the attack elevates privileges to allow remote control of the server from which the malicious code is dropped and run, after which it awaits direction by the bot’s command and control. The binary connected to two hardcoded addresses running on China Telecom, while anyone whose server has been infected will probably notice poor performance.
The bot had been used to launch a number of DDoS attacks during 2014, including a significant one that reached a peak of 119Gbps, on entertainment websites.
Corralling Linux servers for DDoS is a relatively new tactic and this particular campaign appeared to be in its early stages and prone to instability, Akamai said, urging admins to patch and harden vulnerable Linux servers as soon as possible.
"We have traced one of the most significant DDoS attack campaigns of 2014 to infection by IptabLes and IptabLex malware on Linux systems," said Akamai senior vice president and general manager, Security Business, Stuart Scholly.
"This is a significant cybersecurity development because the Linux operating system has not typically been used in DDoS botnets. Linux admins need to know about this threat to take action to protect their servers."
In Akamai-Prolexic’s view, the gang behind this malware was likely to expand their targeting of vulnerable Linux servers, as well as broadening the list of targets.
Detection and remediation? Antivirus doesn’t appear to be a reliable option – only two out of 52 engines picked it up as of May 2014 when the firm started monitoring the threat and by September that had only risen to 23 out of 54. Victims will, of course, notice IptabLes or. IptabLex running.
Prolexic has published a method involving a pair of bash commands and a reboot, so getting rid of this isn’t hard. As for mitigation, the firm recommend rate limiting and has added a rule to the YARA open source tool for good measure.
The most important message is still the need to patch. Don’t leave Linux to rot.
View the original article here
Over a thousand major enterprise networks and small and medium businesses in the U.S. have been compromised by a recently discovered malware package called "Backoff" and are probably unaware of it, the U.S. Department of Homeland Security (DHS) said in a cybersecurity alert on Friday.
Backoff first appeared in October 2013 and is capable of scraping the memory contents of point of sales systems -- industry speak for cash registers and other terminals used at store checkouts -- for data swiped from credit cards, from monitoring the keyboard and logging keystrokes, from communicating with a remote server.
"Over the past year, the Secret Service has responded to network intrusions at numerous businesses throughout the United States that have been impacted by the "Backoff" malware," the alert said. "Seven PoS system providers/vendors have confirmed that they have had multiple clients affected."
The malware is thought to be responsible for the recent data breaches at Target, SuperValu supermarkets and UPS stores, and the Secret Service is still learning of new infections.
DHS first warned of Backoff in late July, when it noted the malware was not detectable my most antivirus software. That made it particularly difficult to stop, because much of the fight against computer viruses and malware rests on antivirus applications.
Most antivirus packages now detect Backoff, but DHS is advising network operators take immediate action to ensure they haven't been affected.
"DHS strongly recommends actively contacting your IT team, antivirus vendor, managed service provider, and/or point of sale system vendor to assess whether your assets may be vulnerable and/or compromised," it said. "The Secret Service is active in contacting impacted businesses, as they are identified, and continues to work with and support those businesses that have been impacted by this PoS malware."
In many cases, hackers gained access to machines through brute-force attacks on remote log-in systems offered through companies like Microsoft, Apple and Google and other third-party vendors. Once inside, they were able to copy the malware to the machine and set it capturing credit card data.
The DHS asked that instances of it are reported to a local Secret Service field office.
The Target data breach was one of the largest in recent memory, resulting in tens of millions of credit and debit cards being compromised. In the last couple of weeks, SuperValu said that at least 180 of its stores had been hit by a data breach and earlier this week UPS said 51 of it UPS Store locations had been hit.
View the original article here
